The breakdown of boundaries between our personal and professional lives has drastically changed how the corporate environment looks. While digital footprints have always been a concern for personal privacy and safety, the digital trails of an organization’s individuals can significantly impact security posture and business outcomes in today’s modern world.
Several factors have accelerated the expansion of digital footprints and the inherent risks they pose for organizations. Follow along as we explore five factors that have intensified the risks associated with digital footprints.
1. Artificial Intelligence (AI)
One of the primary conversations happening in the security space right now is how AI is positively and negatively impacting cybersecurity. AI is a powerful force that has revolutionized how we interact with technology, consequently affecting digital footprint risk.
AI-driven systems learn from user interactions to personalize digital experiences. These systems collect vast amounts of user data to create detailed profiles encompassing personal preferences, online behaviors, and sensitive information. AI’s data-centric nature requires this information to be stored in databases and cloud services, creating attractive targets for cybercriminals.
Not only does AI allow for the continuous collection of information, but it also enables threat actors to do previously manual things more quickly and extensively. They can look at hundreds of websites and use keywords to discover passwords, where someone travels, where they work, what bank accounts they use, and what they buy. Balancing the benefits of AI with the need for data security will continue to be a paramount challenge.
2. Internet of Things (IoT)
IoT has ushered in a new era of interconnected devices, transforming how we interact with technology and the world around us. The average number of IoT devices per person in North America has grown from 8.2 in 2018 to 13.4 in 2023. By 2025, it is forecasted there will be more than 75 billion IoT-connected devices in use.
As the number of IoT devices in our lives multiplies, so does the scale of our digital footprints. From smart thermostats to wearables and home security systems, IoT devices continuously gather and transmit data, often including personal information and usage patterns. Many IoT devices aren’t protected well from a cybersecurity sense and provide easier entry points for cybercriminals, leading to unauthorized access to personal information and control over connected systems.
Average number of devices per person worldwide (2018 vs 2023)
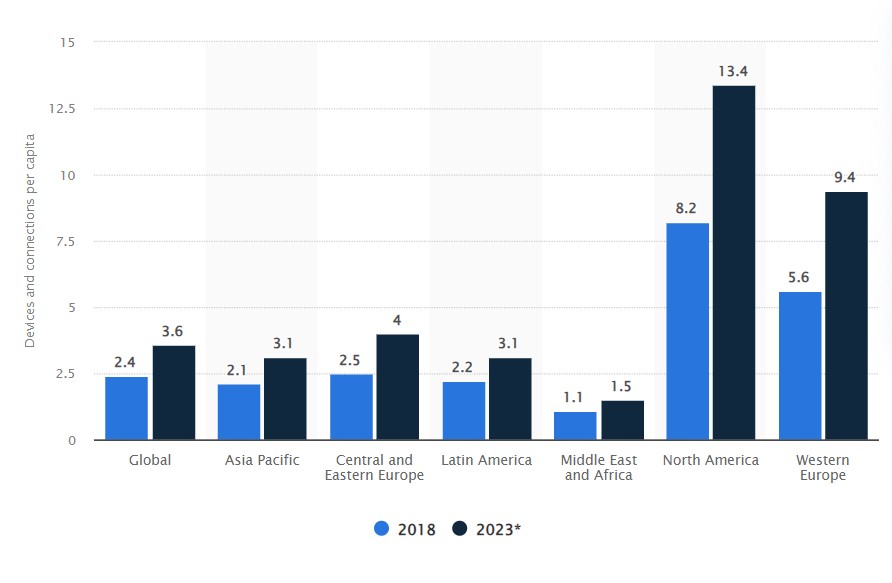
Source: Statista, 2023
3. Remote Work
Remote work is the paradigm of many current organizations and has transformed the way we interact with the digital world. In 2023, 13% of full-time employees work completely remotely, and an additional 28% work in a hybrid model. There are a few ways that the shift to remote work impacts digital footprint risks:
Employees are operating outside the protective confines of a company’s firewalls and security measures
Employees who work in remote or hybrid environments are more vulnerable because they are no longer under the protective shield of in-office security tools and firewalls. Instead, they must now rely on their own routers and security measures for protection.
Remote work relies on using more online tools for connectivity & collaboration
The shift to remote work has necessitated a vast array of digital tools and platforms. From video conferencing to project management software, employees have come to depend on an intricate digital infrastructure to facilitate effective communication. Each new tool that is added leaves behind a digital trail of activities, interactions, and data – all expanding the online presence of employees.
Remote work has propelled the growth of social media and online networking
With more professionals working from home, the reliance on platforms like LinkedIn and Twitter has surged, allowing individuals to build and expand their digital personas. These platforms not only serve as outlets for personal expression but have also evolved into essential professional networks, further amplifying our digital footprint on the global stage.
4. Bring Your Own Device (BYOD)
BYOD policies have introduced a new level of convenience and flexibility to the workplace, allowing employees to use their personal devices for work-related tasks. However, having unclear boundaries between personal and professional devices has significant implications for the security of sensitive corporate data.
When employees store work-related data alongside personal information, they create a digital tangle that leaves organizations vulnerable to breaches and unintentional data exposure. Personal devices often lack the rigorous maintenance and updates that company-owned hardware receive, making them more susceptible to security vulnerabilities.
5. Cloud/SaaS
The transition to cloud computing represents a double-edged sword for organizations in terms of cybersecurity. On one hand, it offers immense advantages in terms of scalability, accessibility, and cost-efficiency. However, on the flip side, it expands the digital footprint and elevates the risk profile.
When organizations move to the cloud, their data is co-located and shared with numerous other users. Everything an organization does in terms of its digital footprint, from sensitive business data to personal information, is stored here. Sophisticated hackers recognize this shared environment as a lucrative target and aim to exploit vulnerabilities in this densely populated digital space.
Prioritizing Digital Footprint Hygiene
As these forces continue to shape our digital landscape, the expansion of digital footprints and the associated risks are realities that organizations cannot afford to ignore. Our Digital Risk Assessments offer a cost-effective way for you to take control of digital footprint risks and protect the business you’ve built.
Take Control of Digital Footprint Risks.
Know your exposure, take action against it, and minimize the impact that digital footprint risks can have on your business.