
Our Solution.
Take Control of Human Cybersecurity Risks.
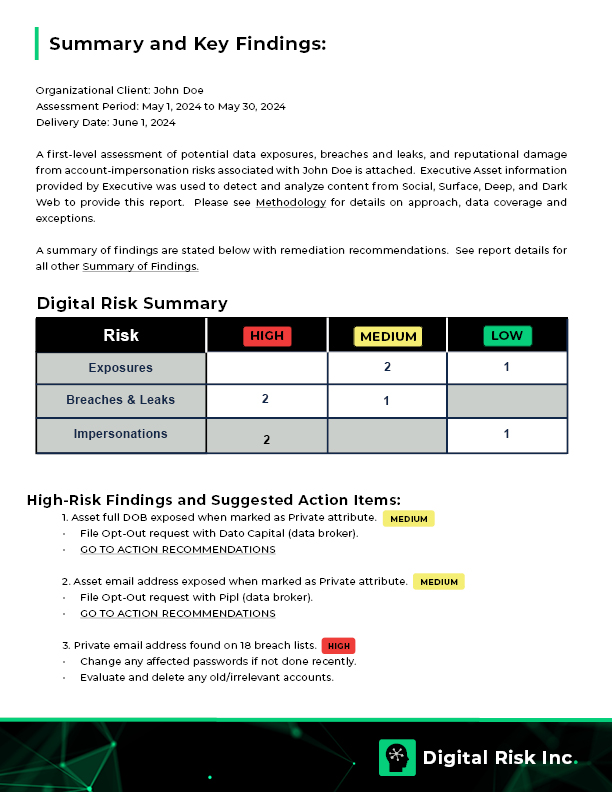
The digital footprints of your executives and employees can lead to a number of digital risks, including exposures, data breaches, and impersonations. These all create opportunities for bad actors to access and exploit your company’s systems and information.
With Digital Risk Inc., take control of human cybersecurity risks to protect the business you’ve built.
How It Works.
Digital Footprint Enrichment
All we need is an email address. We’ll uncover additional exposed digital identifiers to capture a full picture of the vulnerable digital footprint.
Risk Identification & Scoring
We’ll automatically identify and score exposures, data breaches, and impersonations related to the digital footprint.
Remediation Recommendations
You’ll receive a report of summarized and prioritized risks. Plus, we provide remediation guidance to reduce risks now and in the future.
Protect The Business You’ve Built.
- Know your exposure, take action against it, and minimize the impact that Digital Footprint Risks can have on your business.
- Strengthen customer trust by going above and beyond to reduce risk.
- Address security requirements and expectations to sustain and thrive in today’s business environment.
- Reduce your chances of experiencing a cyber attack and continue growing your business.
Frequently Asked Questions.
What are digital footprints composed of?
Digital Footprints are the sum of all the data we leave behind when using the Internet. They consist of Personally Identifiable Information (PII) such as names, dates of birth, home addresses, phone numbers, and user behaviors.
While individual pieces of this data may seem innocuous, bad actors can compile this information to create a complete profile of their target. The more digital footprint information an attacker has for a target, the easier it is to compromise the victim and cause severe damage.
How can digital footprints impact my business?
The hard reality is that humans are every company’s weakest point. Bad actors can exploit information linked to the digital footprints of your executives and employees to gain access to your entire business, its systems, and its information.
Once bad actors have access, they can perform several malicious actions, such as stealing sensitive information, installing malware or ransomware, and deleting critical data. These attacks have far-reaching consequences, including financial losses, operational disruption, legal ramifications, and broken customer trust.
What risks are associated with digital footprints?
Three common digital footprint risks include data breaches, exposures, and impersonations.
Data Breaches:
Data breaches occur when sensitive information is stolen, accessed, or disclosed – either by bad actors with unauthorized access or through negligent or malicious insiders. Instead of piecing together data bit by bit, data breaches typically involve entire datasets with multiple pieces of information for a large group of people. Data breaches provide bad actors with a treasure trove of information, including system credentials and personal data, which fuel attacks such as identity theft, financial fraud, phishing attacks, and direct systems compromise.
Exposures:
Exposures are similar to data breaches as they both involve the disclosure of private information. Unlike data breaches, which typically involve an incident that triggers an alarm, exposures happen quietly and gradually. This often leaves people and businesses unaware that their information is circulating freely. For instance, exposures might occur when a data broker publishes an individual’s PII or someone casually mentions sensitive details on a public forum. If left unaddressed, these exposures enable bad actors to compile detailed profiles that can fuel their malicious attacks.
Impersonations:
Impersonations involve using one person’s identity to compromise another person along the information chain. They include fake social media profiles, email accounts, or online personas that trick others into believing they are interacting with a legitimate person. Bad actors can use impersonation tactics for several nefarious activities, such as spreading misinformation, carrying out scams, or conducting cyber attacks like phishing or Business Email Compromise (BEC). The goal is often to gain access to sensitive information, manipulate individuals into taking specific actions, or tarnish the reputation of the individual and their organization.
Where do your analysts look for digital footprint risks?
We look for exposures, breaches, leaks, and impersonations on the surface/deep web (social media, blogs, forums, data brokers, publications, etc.) and on the dark web, where cybercriminals trade and sell information.
How can I get started?
We’d love to meet with you to discuss how our solution can help you take control of digital footprint risks. Please schedule a meeting here, and we will work with you to get started.
How often should Digital Risk Assessments be conducted?
The frequency of Digital Risk Assessments depends on your company’s specific needs and risk tolerance.
For those seeking regular insights into their company’s digital footprint risk, a monthly assessment provides up-to-date information and allows for timely adjustments to security measures.
Alternatively, quarterly or annual assessments are for those looking to understand their risk holistically over time. Our flexible delivery options cater to your preferences, ensuring you receive the insights you need to manage digital footprint risks effectively.
Let’s Meet.
We’d love to meet with you to discuss how we can help you take control of digital footprint risks.